A user of a low-level cybercriminal forum is selling access to a database of phone numbers belonging to Facebook users, and conveniently letting customers look up those numbers by using an automated Telegram bot.
Although the data is several years old, it still presents a cybersecurity and privacy risk to those whose phone numbers may be exposed—one person advertising the service says it contains data on 500 million users. Facebook told Motherboard the data relates to a vulnerability the company fixed in August 2019.
"It is very worrying to see a database of that size being sold in cybercrime communities, it harms our privacy severely and will certainly be used for smishing and other fraudulent activities by bad actors," Alon Gal, co-founder and CTO of cybersecurity firm Hudson Rock, and who first alerted Motherboard about the bot, said.
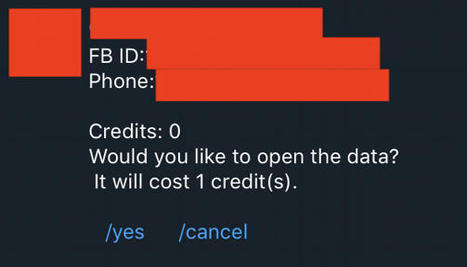
Upon launch, the Telegram bot says "The bot helps to find out the cellular phone numbers of Facebook users," according to Motherboard's tests. The bot lets users enter either a phone number to receive the corresponding user's Facebook ID, or visa versa. The initial results from the bot are redacted, but users can buy credits to reveal the full phone number. One credit is $20, with prices stretching up to $5,000 for 10,000 credits. The bot claims to contain information on Facebook users from the U.S., Canada, the U.K., Australia, and 15 other countries.



 Your new post is loading...
Your new post is loading...






A new phonebook business model ?