Society doesn't work without trust
Human being is the only species with trust. We trust hundreds of strangers without even thinking about it.
How do we enable trust?
How does security enable trust. How do we induce trust?
- Trusting friends is about who they are as persons.
- Trusting strangers is about their actions
Trust: confidence, consistence, compliancy. It's about cooperation.
- We trust people, companies and systems
- We trust systems to produce expected behaviors
All complex ecosystems require cooperation. In any cooperative system, there is a way to subvert the system for personal interests.
These are called defectors in game theory. They are parasites. They can survive if they are contained. If too many parasites the body dies and the parasites die too.
Society doesn't work if everybody steals. Security can be defined as a tax on the honests.
Social species: individual competition plus group competition.
Security is to keep defection level at an acceptable minimum that is not zero.
NSA defector Edward Snowden raises moral debates but the point is that he is a defector. How group enforce the norm. Even mafia groups.
It is about societal pressure.
4 types of societal pressure
- moral: we don't steal because we know stealing is wrong.
- reputation: also in our heads but link to other's reactions. Humans are the only species to transmit reputation.
Experiment: coffee machine + honesty box. Putting a photograph of a pair of eyes in the box bottom decreased the cheat rate dramatically - laws: formalizing reputation, and focusing only on penalties (because of the cost implied by rewarding the majority of honest people). With exceptions in the shape of tax breaks
- technology: security systems. Door locks, alarms, ... Some of them extending globally. ATM cards are protected globally.
Example: eBay feedback mechanism is a reputational security system that worked remarkably for years as the main security system.
How does technology affects us?
Technology is what allows society to scale. It is neutral.
Filesharing: social pressure vs technology
Attackers have a first mover advantage and are more adaptive.
Mid 90's Internet going commercial: hackers used it immediately while it took 10 years to the police to figure out how to address it
Such delay is the main security gap
Our society is at a point where technology is faster than social changes which means that the security gap widens.
Before: buy this and you'll be safe
Now: when you've been attacked, please talk to us and we'll help
It's the antivirus history
Smart paradigm: detect unknown viruses including false positives
Stupid paradigm: check for signatures and update once or twice a day
The stupid paradigm seems to have won.
So technology will always favor defectors? True, but large organizations can now use technology in a much more effective manner.
Our society has the most technology and the largest institutions.
The battle is amplifying between agile defectors and slower yet more effective institutions. Losers are those of us in the middle.
To him it is not even clear how there is a balance nor how it will evolve.
As a conclusion
- there will always be defectors
- ourselves are not 100% cooperative, we all defect some time in a way
- law of diminishing returns
- there are good and bad defectors and history decided afterwards. That will be the case for Edward Snowden
- society need defectors. This is how we evolve. Defectors are at the forefront of social change: freeing the slaves, giving women voting rights



 Your new post is loading...
Your new post is loading...










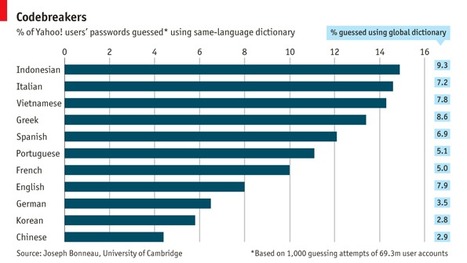


Impressive exploit given Apple's increased fortress walls thickness. Yet (why) should you jailbreak ?