 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Have you heard of something called cyber hygiene? Surely, brushing your teeth and taking showers isn’t something traditionally associated with technology — yet the term is a useful metaphor for needing to make smart decisions about your smart devices.
Good hygiene is something you’re taught as a child and something that generally sticks with you for the rest of your life. It involves three basic principles: using products and tools that fit your hygiene needs, performing these hygienic tasks correctly, and establishing a routine.
But what is cyber hygiene and what does it have to do with your computer and connected devices?
Cyber hygiene is about training yourself to think proactively about your cyber security — as you do with your daily personal hygiene — to resist cyber threats and online security issues. Unfortunately, cyber security still isn’t taken as seriously as cavities and root canals. Some people take cyber security for granted, but this may change, as cyber threats continue to evolve. In the meantime, establishing solid cyber hygiene practices should be as routine as brushing your teeth.
Here are a few tips to get you and your family thinking about good cyber hygiene practices. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/?s=cyberhygiene https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Cyber-Hygiene

|
Scooped by
Gust MEES
|
Aside from cool cat feeders, it is possible to find multiple maker projects for controlling garage doors, blind windows, smart locks, tracking cars, control temperature and humidity levels, and so on. However, the security aspect of these devices needs to take some extra attention, starting from the connection between the device and the Cloud infrastructure. Most microcontrollers today are not powerful enough to handle secure connections, like SSL or TLS, so all the communication between the device and the server is open to attacks, like sniffing values, tacking device credentials, faking values, granting unauthorized access to physical facilities, unlocking doors, and many other possibilities. This way, securing the communications for all the Internet-connected devices should be a priority, especially if they can jeopardize our security or privacy.
The security of the Internet of Things does not only rely on secure communications, but it is a great start. The maker community must be aware of the security concerns of untrusted communications, and must have the appropriate resources to handle it. This way it is common to see different alternatives to offer secure communications in the microcontrollers, like porting SSL/TLS libraries to cheap devices like ESP8266, or device vendors that already integrates a crypto chip that process all this stuff by hardware, like the recent Arduino MKR1000.
In thinger.io we are concerned about this security aspect, so our cloud supports secure connections for any device with this capability. In the recent Arduino library update, starting from version 2.4.1, we have introduced support for the Arduino MKR1000, including secure TLS connections by default. Just start with the following sample sketch for the MKR1000, and you will have encrypted connections by default. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=ARDUINO https://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=IoT

|
Scooped by
Gust MEES
|
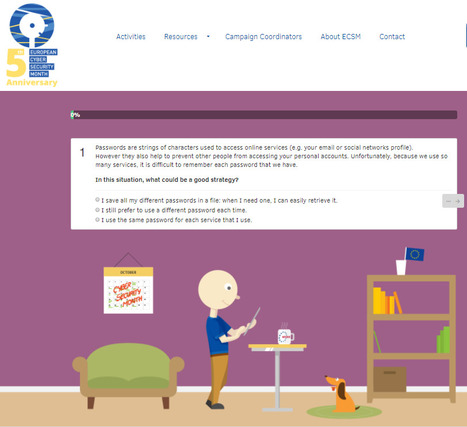
Mit sicheren Passwörtern private Daten schützen
Jedes Jahr erinnert der 1. Februar als "Ändere dein Passwort"-Tag Bürgerinnen und Bürger daran, ihre Passwörter zu wechseln. Passwörter sind aus dem digitalen Zeitalter nicht wegzudenken: Mit ihnen schützen wir Accounts für E-Mails und Online-Shops, Zugänge zum Online-Banking und zu sozialen Netzwerken, das eigene Smartphone und das WLAN zuhause.
Umso wichtiger ist es, all die dort hinterlegten privaten Daten mit sicheren Passwörtern vor dem Zugriff durch Dritte zu schützen – und sich diese Passwörter gut merken zu können. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Passwords

|
Scooped by
Gust MEES
|
The solution for Smeets and his team though is not to pile on extra layers of authentication, but rather to distribute them. And that's where blockchain comes it. Because the blockchain functions via a distributed and encrypted ledger shared across all of a network's users and devices, it creates a network of authentication that is verifiable and not easily hacked. With blockchain implemented, a device cannot access a network unless it is verified through the entire ledger. In this scenario attacks like Mirai become significantly more difficult, if not impossible, because a hacker would need to modify the entire ledger, and not just the credentials of any one device.
Ericcson Research demonstrated a proof-of-concept of this idea at the 2017 Mobile World Congress in Barcelona this past March. The researchers set up a small WiFi network that used blockchain authentication instead of a typical username/password setup. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=blockchain

|
Scooped by
Gust MEES
|
There is no doubt that companies of all shapes and sizes are increasing their spend in internet-of-things (IoT) technology. In fact, IDC projects this to be a $1.4 trillion market by 2021. With the increased spend and demand by consumers for low-price and high-value IoT devices, makers of these connected technologies have put a premium on affordability. The race to the bottom on price has inadvertently created major risks for organizations and consumers, according to PwC’s “Uncovering the Potential of the Internet of Things” report.
The pressure is on, and we see many makers of connected devices that produce IoT products as inexpensively as possible skipping important steps such as the design of security and privacy protections. This is generating significant new risks that are not widely understood during a time when consumers are more concerned about price than privacy and security. Risks include physical, software, encryption and network attacks, all of which could have wide-ranging effects on our daily lives, from taking over a connected car to obtaining sensitive data from a connected home to accessing a private network via a wearable device. Also, there are societal concerns, including getting access to valuable intellectual property, sabotage to companies or governments and espionage. Consumer-focused companies need to ensure they are meeting their customers’ concerns. Simply put, the proper cybersecurity and privacy measures can aid businesses in seeing the full potential of IoT. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=IoT http://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Zombiecomputer und wie Sie sie vermeiden:
Sie haben wahrscheinlich das Wort Botnetz in letzter Zeit mehr als einmal gehört, und das überrascht kaum. Jedes verbundene Gerät kann zombifiziert werden — und Teil eines Botnetzes werden. Das schließt PCs, Smartphones, Tablets, Router, WLAN-Kühlschränke, Smart Toys und viele andere Geräte ein.
In diesem Post erklären wir, was ein Botnetz ist, was es anrichtet und wie Sie Ihre Geräte davor schützen, Teil eines Botnetzes zu werden.
Botnetze: Was sind sie?
Ein Botnetz ist eine Gruppe von Geräten, die mit dem Internet verbundenen sind und mit einer bestimmten Malware infiziert wurden. Die Art von Malware, die Bots, oder Zombies, erstellt, arbeitet verdeckt, erwirbt Administratorenrechte und übergibt den Cyberkriminellen die Kontrolle, ohne sich zu verraten. Das infizierte Gerät funktioniert wie gewöhnlich – aber es folgt auch gleichzeitig den Anweisungen des Kommandeurs des Botnetzes. Zusammen bilden die infizierten Geräte eine starke Infrastruktur, mit der Cyberverbrechen begangen werden können.
Einige Botnetzkommandeure spezialisieren sich nur auf den Support und die Verbreitung des Botnetzes. Sie vermieten diese schädlichen Tools an andere Kriminelle, die mit ihnen Angriffe und andere kriminale Taten durchführen. Hier sind die vier gängigsten Wege, um ein Botnetz zu verwenden. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=Botnet https://twitter.com/search?src=typd&q=%23fscd

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Les malwares Windows sont souvent plus connus et fréquemment mis en avant dans les différents rapports d'experts en sécurité. Néanmoins, les menaces sont bien réelles et tout aussi dangereuses dans les environnement Linux, MacOS et Android.
Les experts en sécurité ont tendance à mettre l’accent sur les malwares de Windows, qui est traditionnellement plus visé par les activités malveillantes. Mais alors que certains rapports ne se concentrent que sur l’environnement Microsoft, les menaces sont bien présentes sur Linux, MacOS et les équipements Android, et moins bien appréhendées. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security http://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
Botnets
Botnets have existed for at least a decade. As early as 2000, hackers were breaking into computers over the Internet and controlling them en masse from centralized systems. Among other things, the hackers used the combined computing power of these botnets to launch distributed denial-of-service attacks, which flood websites with traffic to take them down.
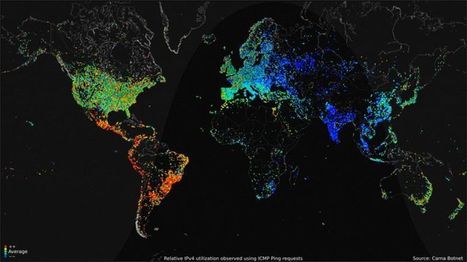
But now the problem is getting worse, thanks to a flood of cheap webcams, digital video recorders, and other gadgets in the "Internet of things." Because these devices typically have little or no security, hackers can take them over with little effort. And that makes it easier than ever to build huge botnets that take down much more than one site at a time. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
|

|
Scooped by
Gust MEES
|
Les contrôles d’accès censés protéger les données personnelles comme le carnet d’adresses peuvent être contournés, comme vient de le démontrer un chercheur en sécurité.
Depuis hier, 24 septembre, les utilisateurs d’ordinateurs Mac peuvent installer la dernière version du système d’exploitation macOS Mojave. Malheureusement, celle-ci est déjà impacté par une importante faille de sécurité qui met à mal la protection des données personnelles. Avec macOS Mojave, Apple a en effet musclé les contrôles d’accès aux fichiers et aux applications sensibles tels que le carnet d’adresses, l’historique des messages, la base de données d’email, le microphone, la caméra, etc. Mais ces contrôles d’accès peuvent être court-circuités, comme le démontre le chercheur en sécurité Patrick Wardle.
Cet expert a développé une application baptisée « breakMojave » capable de siphonner en douce le carnet d’adresses de l’utilisateur sans rien lui demander. Il a montré le déroulement du hack dans une vidéo Vimeo. Au départ, on constate qu’aucune application tierce n’a accès au carnet d’adresses. Le chercheur ouvre ensuite une fenêtre Terminal et tente d’accéder directement aux données du carnet d’adresses, sans succès. Le lancement de breakMojave provoque enfin l’extraction des données, qui se retrouvent copiées en vrac sur le bureau. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
The Security Education Companion is a resource for people teaching digital security to their friends and neighbors. Lesson Topics These lesson modules are centered around specific learning objectives, and are divided into beginner, intermediate, and advanced lessons. Before jumping into using these modules, we recommend reading the articles from Security Education 101.
Within each of these modules, we have suggested prerequisites, warmups, activities, talking points, graphic materials, anticipated Q/A, as well as accompanying guides from Surveillance Self-Defensefor tool configurations and installs. As you get more practice with digital security workshops, we encourage you to remix or repurpose these lessons how you see fit. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/?s=5+minutes

|
Scooped by
Gust MEES
|
Off the paths it is almost impossible to find anything – unless you know what you’re looking for – so it feels a bit like a treasure hunt. Because really the only way to find anything in this vast forest is to be told where to look. This is how the dark web works – and it is essentially the name given to all the hidden places on the internet.
Just like the forest, the dark web hides things well – it hides actions and it hides identities. The dark web also prevents people from knowing who you are, what you are doing and where you are doing it. It is not surprising, then, that the dark web is often used for illegal activity and that it is hard to police. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=Darknet http://www.scoop.it/t/securite-pc-et-internet/?&tag=darknet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Early Friday morning the world experienced the year’s latest cyberattack. Starting first in the United Kingdom and Spain, the malicious “WannaCrypt” software quickly spread globally, blocking customers from their data unless they paid a ransom using Bitcoin. The WannaCrypt exploits used in the attack were drawn from the exploits stolen from the National Security Agency, or NSA, in the United States. That theft was publicly reported earlier this year. Learn more / en savoir plus / Mehr erfahren: https://gustmees.wordpress.com/?s=cybersecurity https://gustmees.wordpress.com/?s=5+minutes

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
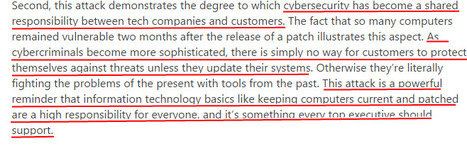
Today, half of America’s internet shut down when hackers unleashed a large distributed denial of service (DDoS) attack on the servers of Dyn, a major DNS host. It’s still unclear exactly who carried out the attack and why, but regardless, the event served as a demonstration of how easily large swaths of the web can be wiped out if attacked by determined hackers. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
|



 Your new post is loading...
Your new post is loading...






















Have you heard of something called cyber hygiene? Surely, brushing your teeth and taking showers isn’t something traditionally associated with technology — yet the term is a useful metaphor for needing to make smart decisions about your smart devices.
Good hygiene is something you’re taught as a child and something that generally sticks with you for the rest of your life. It involves three basic principles: using products and tools that fit your hygiene needs, performing these hygienic tasks correctly, and establishing a routine.
But what is cyber hygiene and what does it have to do with your computer and connected devices?
Cyber hygiene is about training yourself to think proactively about your cyber security — as you do with your daily personal hygiene — to resist cyber threats and online security issues. Unfortunately, cyber security still isn’t taken as seriously as cavities and root canals. Some people take cyber security for granted, but this may change, as cyber threats continue to evolve. In the meantime, establishing solid cyber hygiene practices should be as routine as brushing your teeth.
Here are a few tips to get you and your family thinking about good cyber hygiene practices.
Learn more / En savoir plus / Mehr erfahren:
https://gustmees.wordpress.com/?s=cyberhygiene
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Cyber-Hygiene